Uncover inefficiencies. Unleash potential.
Gain clear operational insights to boost margins and align effortlessly with your goals — all from a single objective source.
Drive unparalleled success with operational clarity
Streamline reporting
Save valuable time and eliminate friction with automated reporting to your team and PE stakeholders.
Achieve operational excellence
Quickly diagnose operational challenges, continuously monitor performance, and uphold best practices for sustainable growth.
Align key stakeholders
Unite stakeholders with a single, real-time source of truth, ensuring accessible and consistent insights.
Enhance profitability
Understand profitability by various components (SKUs, sales person, region, etc.)
From install to insights in hours
Get initial process insights in as little as hours, with no lift from your team.
- Push button install
- Automatic data ingestion
- Automatic process mapping
- No system degradation
- No down time
Seamless access to business insights
Uncover continuous business insights down to the customer or unit level — without the hassle of data collection and reporting — in areas such as:
- Sales Effectiveness
- Order to Cash Efficiency
- Services
- Item Velocity
- Procurement Efficiency
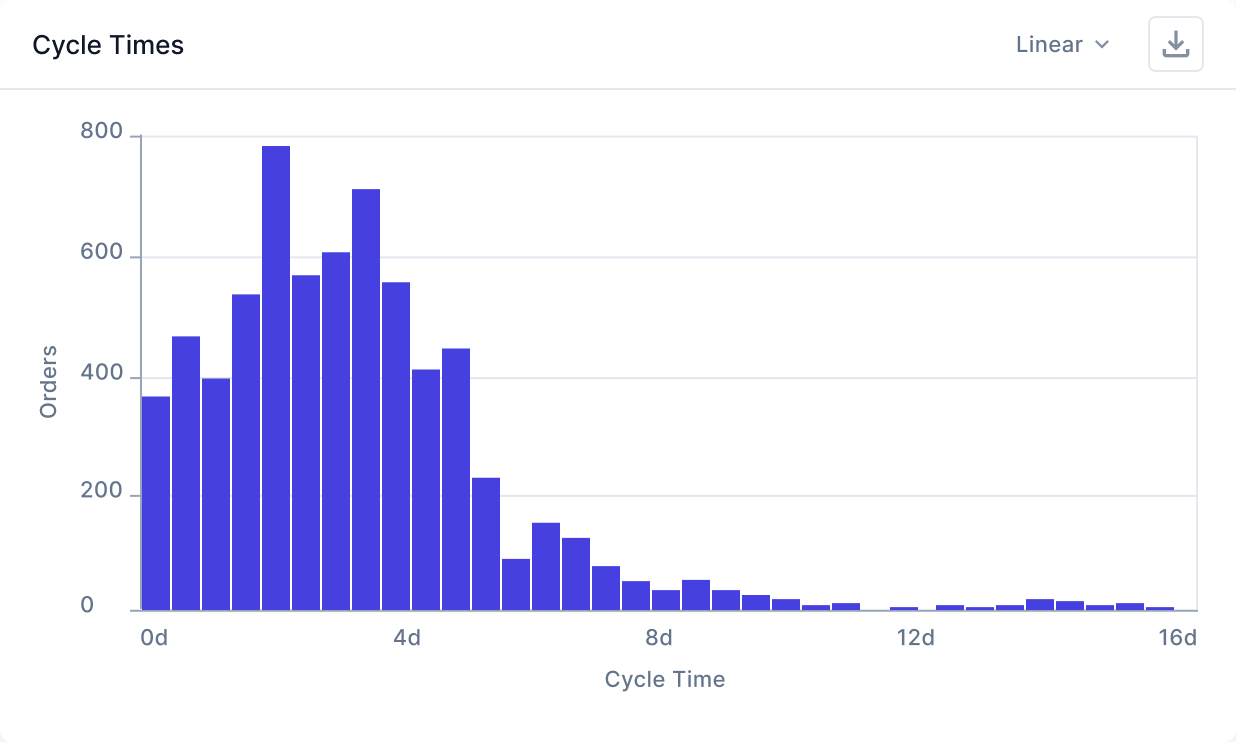
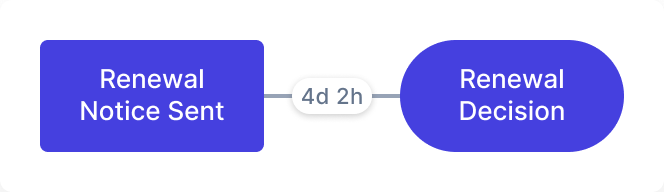
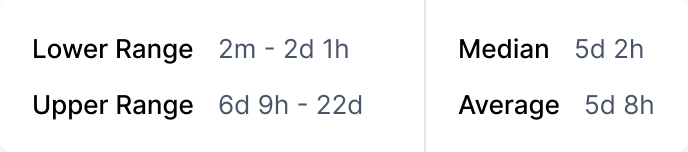
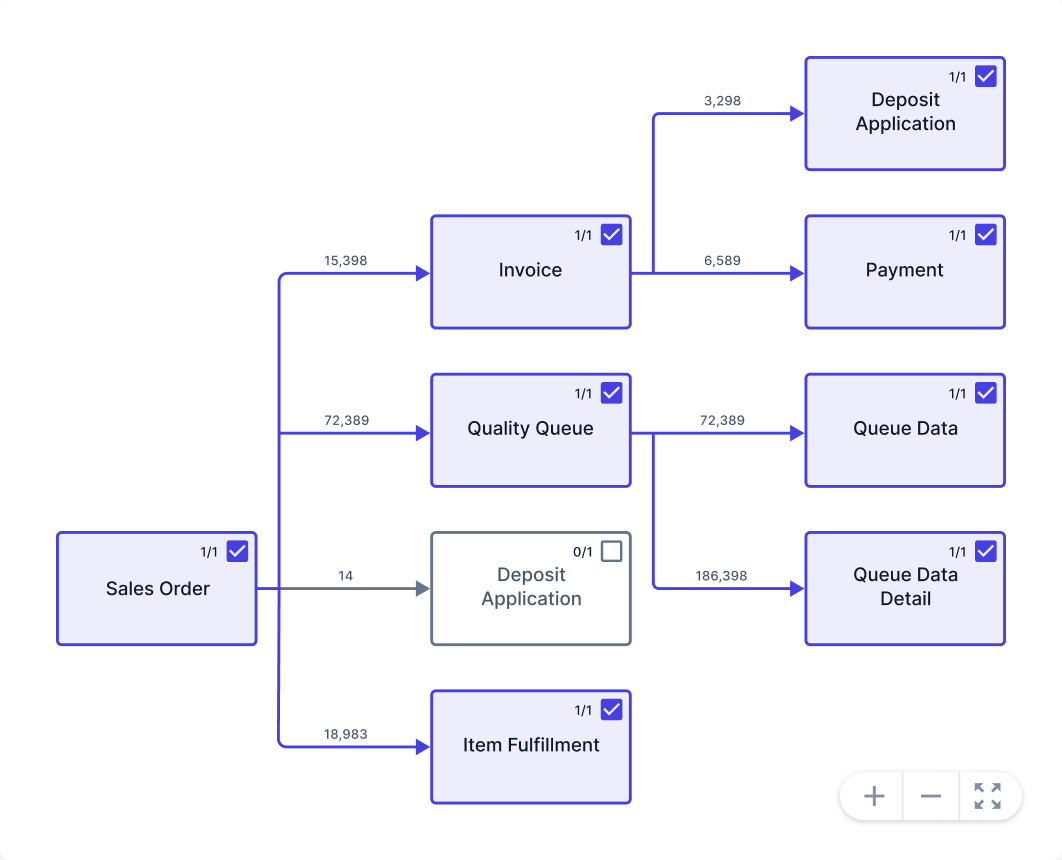
Real-time action.
Clear paths to profit.
Take informed actions and measure their impact in real-time, paving a clear path to improved profitability.
You’re in good hands
Your privacy and security equal our success. (It’s also just the right thing to do.)




Commonly asked questions
Chassi has located its production environment within the US-East-1 (N. Virginia) region of the Amazon Web Services (AWS) Elastic Compute Cloud (EC2). The customer-facing application runs on servers that are physically and logically secured from other components of the Chassi corporate infrastructure.
AWS provides serverless technology architecture and short term and long-term data storage. Data center facilities undergo regular SOC 2 Type 2 audits.
- Web Development Best Practices
- Development Environment Authentication
- Strong Network Access Controls
- Protection Against Injection Attacks
- OWASP Top10 Defenses
- Knowledgeable Security Professionals
All sensitive data transmitted and processed within Chassi’s production environment is encrypted to protect sensitive data against third-party disclosure in transit and at rest (stored and backup) using strong encryption technologies.
- User access lists for applications, network storage, root accounts and databases are reviewed on a regular basis.
- Security training
- Chassi maintains a security awareness program through various mechanisms including:
- The security assurance application which publishes and tracks employee training
- Annual information security awareness training
- Chassi maintains a security awareness program through various mechanisms including:
- Antivirus is installed on all workstations. Suspicious activity trigger alerts are sent to responsible information security staff.
No. We don’t touch the GL or any financials. There are no write features to the application.
At the end of the Health Check or engagement, we delete the data. That’s it.
Experience the Chassi difference
Schedule a demo today and learn how Chassi can streamline processes and boost margins.
